Blog Posts

Emerging Threats in the Digital Age: Spice Up Your Cybersecurity
In a world where technology rules, emerging threats in the digital realm are like hidden landmines, waiting for the right moment to explode. Cybercriminals are

Android Users, Beware! Government’s Urgent Warning – Is Your Smartphone on the Hit List?
For Android enthusiasts, the Indian government has sounded the alarm on a pressing issue, affecting popular smartphone giants such as Google Pixel, Samsung, and OnePlus,

Alarming Rise in Cybercrime: Bengaluru’s Rs.470 Crore Battle Against Fraudsters
In recent months, Bengaluru residents have faced a growing threat from cyber fraud, resulting in significant financial losses. This blog post delves into the data,
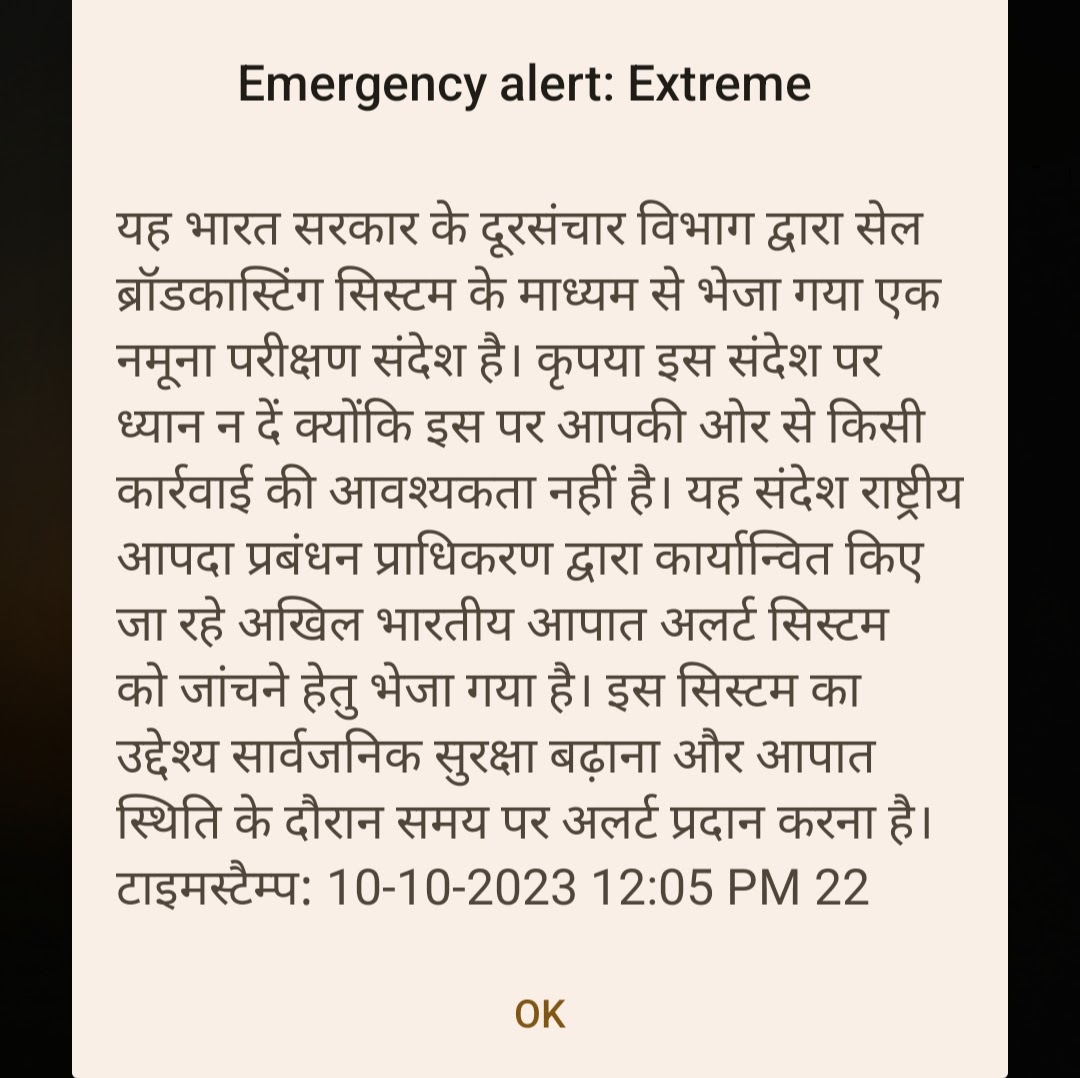
Have you received an ‘Emergency alert: Severe’ message on your phone? Here’s what it means.
The Department of Telecommunication recently sent out a practice message to all mobile phones as a test. On Thursday around 1:30 pm, several smartphones received

ISRO faces over 100 hacking attempts daily! Here is a report
The Indian Space Research Organization, known as ISRO, deals with more than 100 cyber attacks every day. The Chairman of ISRO, S Somanath, shared this

5 Essential Measures for Protecting Yourself Against Online Fraud
Online payments have simplified transactions, allowing us to conduct business from anywhere with just a few clicks. However, a single mis-click can lead to significant

€5.5 million fine imposed on WhatsApp for data protection violations
On Thursday, Ireland’s Data Protection Commission (DPC) fined Meta’s WhatsApp a new €5.5 million for violating data protection laws when processing users’ personal data. As
Android devices are being exploited by hackers with RATs
The threat actor behind the BlackRock and ERMAC Android banking trojans has unleashed yet another malware for rent called Hook that introduces new capabilities to

Warning: Tainted VPNs are Distributing EyeSpy Monitoring Software
A compromised VPN installer is used to distribute surveillance software called EyeSpy as part of a malware campaign launched in May 2022. It uses “SecondEye’s

Permissions matter for SaaS Security – Why?
Earlier this year, attackers compromised Mailchimp, a popular SaaS email marketing platform. We examined over 300 Mailchimp customer accounts and exported audience data from 102

Synology releases patch for critical RCE vulnerability affecting VPN Plus servers
Synology has released a security update to address a critical vulnerability in VPN Plus Server that could be used to take over an affected system.

WhatsApp introduces proxy support to help users bypass internet censorship
Popular instant messaging service WhatsApp has introduced support for proxy servers in the latest versions of its Android and iOS apps. This allows users to

Hackers use stolen banking information to trick victims into downloading BitRAT malware
A new malware campaign has been observed using sensitive information stolen from banks as bait in phishing emails to drop a remote access Trojan called
APT hackers use malicious Excel add-ins as an initial breach vector
Microsoft’s decision to block Visual Basic for Applications (VBA) macros by default in Office files downloaded from the Internet has prompted many attackers to improvise

Facebook pays $725 million to settle lawsuit over Cambridge Analytica data breach
Meta Platforms, the parent company of Facebook, Instagram, and WhatsApp, has agreed to pay $725 million to settle a lengthy class-action lawsuit filed in 2018.

The Era of Cyber Threat Information Sharing
We have spent 40 years protecting ourselves as individuals. We tried to trick and outsmart the cybercriminals, but when all our efforts failed, we thought

Over 829 million cyberattacks blocked in Q4
In the fourth quarter (Q4) of 2022, over 829 million cyberattacks were blocked globally, including 59% of Indian websites. According to application security firm Industace,

The Age of Sharing Cyber Threat Intelligence
We have spent 40 years protecting ourselves as individuals. We tried to trick and outsmart the cybercriminals, but when all our efforts failed, we thought

BrasDex is a new Android malware from Casbaneiro Actors
A new Android malware called BrasDex was exposed to users in Brazil as part of a multi-platform campaign. The malware targets a series of Brazilian

85% of attacks now use encrypted channels
According to Zscaler, malware continues to be the biggest threat to individuals and businesses across nine key industries, with manufacturing, education, and healthcare being the
