The past couple of years have seen an upward push in software supply chain attack, with the maximum salient example being the SolarWinds attack. As production environments have gained a couple of layers of safety, and lots of the attention of safety groups, malicious actors have set their points of interest on “poisoning the properly”, i.e., target wherein packages are advanced or their constructing block additives. However, what does this suggest for cloud native? Are cloud native packages more liable to supply chain attacks? Let’s try and solve these questions .
Cloud Native Supply Chain Threats
There are several characteristics of cloud native software improvement environments that lead them to a lucrative goal for attackers seeking to embed malicious code into the supply chain.
First, cloud native utility improvement is characterized by big use of open source components, regularly obtained from public registries. Even as many open supply projects are properly-ruled and scrutinized under many eyes, some are not, and this lets malicious actors masquerade as members. The better up within the supply chain that attackers can cross, the higher their possibilities of achieving giant dissemination of their code, that’s why the greater advanced attackers look for widely used programs that would reappear in lots of distinctive programs.
Additionally, nowadays dev environments are not scrutinized as closely as production environments, and container pictures, features and packages are updated often using CI/CD pipelines, growing multiple possibilities for attackers to embed themselves into the method. group Nautilus has detected and analyzed attacks on CI SaaS environments that abused the CI procedure itself to advantage access to cloud CPU time. From there it’s a rather quick hop into the artifacts being built in those CI pipelines
Observed Attack Vectors
Our cyber studies on attacks in the wild that target containers and Kubernetes environments have proven various degrees of class and evasion strategies. beginning from the quite easy to the extra superior, we’re seeing:
- Placing malicious snap shots in public registries, both for pulling them into compromised environments or within the hope someone will use them.
- Hiding malicious code interior benign, “vanilla” photos, within the desired builders will use them no longer knowing what lurks inside them. We’ve also seen “typo-squatting” used in this regard, where a popular image name is intentionally misspelled – for example TensorFlow in preference to TensorFlow.
- Evading static analysis of malware through the usage of polymorphic, evolving malware that isn’t recognizable based on its signature, and calls in additional components after a photo has been deployed and run as a container.
- Circumventing the controls inside the CI/CD pipeline by constructing snapshots at once on hosts
- Abusing cloud-based totally CI tools, wherein the attackers take gain of free SaaS offerings to run crypto-currency mining under the guise of building an software.
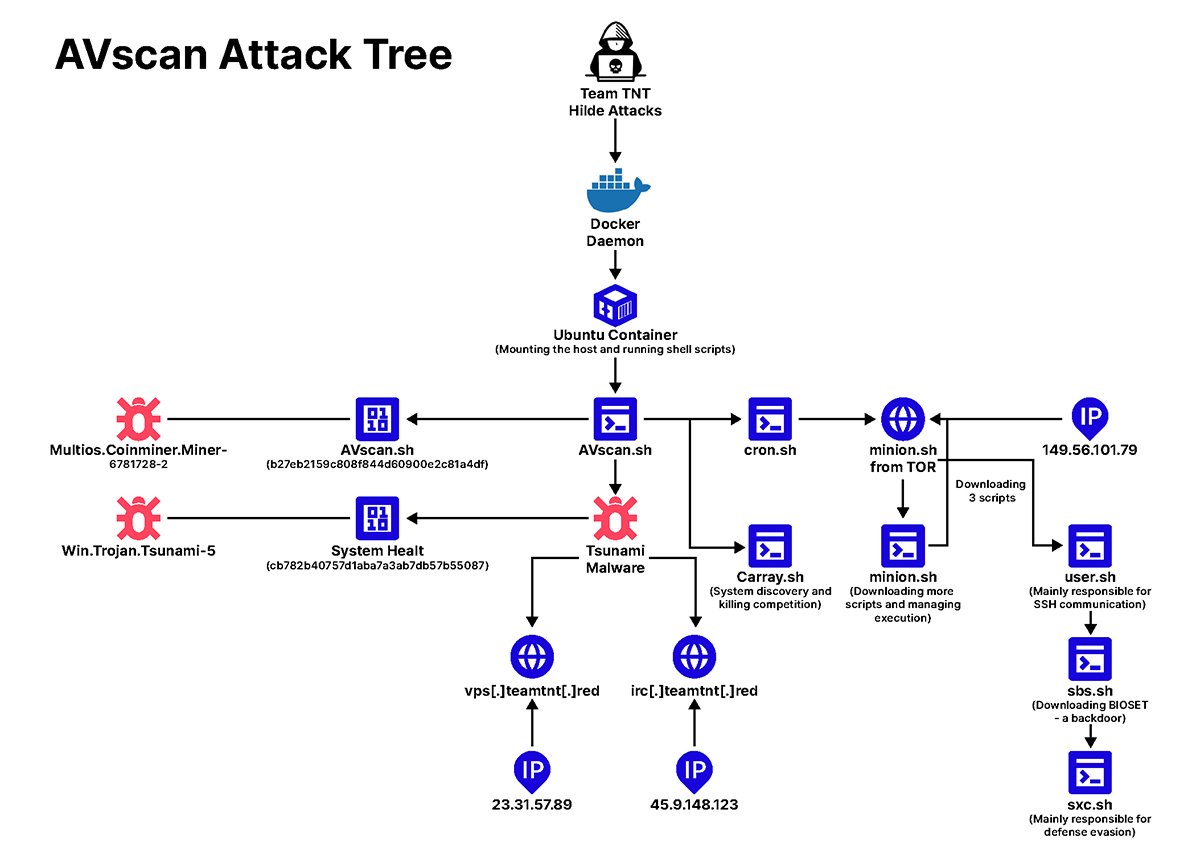
Figure 1: AVScan attack tree showing gradual branching and malware downloads
(Source: Team Nautilus, Aqua)
At diverse levels of those attacks, the malicious actors could perform gradual, an increasing number of extreme moves to achieve their objectives and set up persistence in the environment – i.e., allow them to maintain an attack beyond the particular field, host, or even cluster.
Any Good News in This Scenario?
Thankfully, yes. There are inherent characteristics of cloud native applications that make them extra resilient to attack, and permit to limit the damage of an assault that would slip through in a manner that’s extra sturdy than with conventional, monolithic applications:
- The high degree of automation within the pipeline permits embedding controls that could probably detect or at the least make it harder for supply chain attack to be successful (extra about that in the next section).
- Because of the orchestrated and often ephemeral nature of cloud native workloads, it’s extraordinarily tough for the attacker to persist. whilst an attack just like the SolarWinds attack occurs, and infects a windows server somewhere, that home windows server is probably walking with the identical permissions, identical IP cope with, and no downtime or upgrades for many months, from time to time even years. Through comparison, a serverless characteristic normally runs for seconds, and a maximum of 15 mins in most cloud environments, which would restrict the capacity damage.
- Observability in cloud native is hugely advanced. with open source gear like Tracee, we are able to get very distinct real-time records of approximately every process, each network connection, every occasion. It’s easier to discover anomalies, and simpler to isolate them at a method stage, feature stage, or container stage.
How to Protect Against Supply Chain Attacks
Getting rid of the threat of supply chain attacks is truly impossible – but there are measures that DevOps and safety teams can take to reduce that threat:
Manipulate get admission to to public registries and open source components
Reduce the threat by means of limiting the number of individuals who can get entry to public photographs and programs, and create a curated inner registry for base pics. put into effect a manner to ensure that only trusted images are used.
Digitally sign photographs or use different strategies of keeping dev-to-prod image integrity
Make sure that the images you’re deploying are the identical ones you vetted and prevent the deployment of images outside the predefined pipeline.
Isolate your dev/staging environments
In case your supply chain is correctly penetrated, attackers may try to jump into adjoining environments, even without targeting production environments, for such things as admin credentials, sensitive IP, or supply-code. be sure to authenticate, get right of entry to and restriction it to precise IP addresses (or VPN).
Scan Pictures for malware, the usage of each static and dynamic analysis
While there’s some cost scanning images and features for malware the use of static, signature- or sample-based gear, the extra state-of-the-art attacks now prevent such techniques with the aid of phasing their attacks – embedding small, harmless-looking components inside the image, and then downloading and going for walks additional malware best when the photograph is run as a box.
Such sophisticated attacks are ignored by means of static vulnerability and malware scanning and might handiest be detected through dynamic analysis of the container conduct because it’s running.
Automate and embed safety controls in the CI/CD pipeline
With the quick pace of release cycles, it is essential to embed safety into your development lifecycle properly from the beginning. To trap a supply chain attack early on, you need to detect sudden code execution drifts for your pipeline. For this reason, you may use Tracee, open supply runtime protection tool, which can also discover malicious activity for the duration of the construct, thereby supporting you to secure your applications early inside the development lifecycle.
Screen your runtime surroundings
In case your supply chain is penetrated in spite of all of the above, this will in the end display up as strange interest to your production surroundings. Actual-time runtime protection should be a detail in any method intended to protect against each supply chain attack as well as “ordinary” attacks on production infrastructure and programs.
Conclusion
The fact of the cloud native software program supply chain is that organizations are heavily relying on 1/3-party code, probably introducing inclined and risky components into their applications. This provides masses of possibilities for attackers to goal legitimate software programs thru 1/3 parties and embed themselves into the improvement procedure. Supply chain attacks are right here to live and evolve, and organizations should alter their security practices to detect, identify and mitigate them.