network security audits
Network Security Audit
A community security audit offers organizations a whole evaluation in their protection systems. Those audits permit corporations to fix faults proactively, guard touchy facts, and layout a greater reliable IT safety plan.
This newsletter teaches all you want to recognize approximately community protection audits. You may also discover a community safety audit checklist that will help you look at your security practices and measures. A network protection audit is a technical evaluation of a business enterprise’s network. The audit assessments regulations, packages, and operating structures for safety faults and dangers.
A network protection audit is a technical evaluation of a business enterprise’s network. The audit assessments regulations, packages, and operating structures for safety faults and dangers.
Community auditing is a scientific manner in the course of which an IT professional analyzes five components of a community:
- Network security
- Control implementation
- Network availability
- Management practices
- Overall performance
If the audit discovers any troubles, the agency fixes the trouble earlier than an attacker can make the most the weakness.
Network safety audits can both be manual or automated. an automated audit usually relies on Computer-Assisted Audit Technique (CAAT) software to analyze the system.
Benefits of Network Security Auditing
Security benefits of a community protection audit are:
- Identify potential threats to your system.
- Make sure the protection of precious facts.
- Find hardware troubles.
- Improve vulnerable business enterprise rules and practices.
- Discover network inefficiencies.
Safety benefits apart, an audit also allows make sound business decisions. ordinary checks enable you to discover higher software options and become aware of fee-saving possibilities.
Why are Network Security Audits important?
Security audits are an crucial detail of community security. Community security audits often allow organizations to preserve abreast of the ultra-modern Security threats and vulnerabilities.
Community safety audits can be performed manually through security professionals or automatic using various network trying out gear. Community safety audits are performed to make sure that the networks are comfortable and unfastened from vulnerabilities, security loopholes, or software bugs that hackers can take advantage of.
The first-rate manner to behavior a network safety audit is to have a expert penetration checking out team in order that the network can be scanned and tested thoroughly. A penetration testing crew can perform advanced network safety audits, vulnerability assessments, and penetration checks on a community. network penetration trying out gear are also known as community vulnerability scanners or network security scanners.
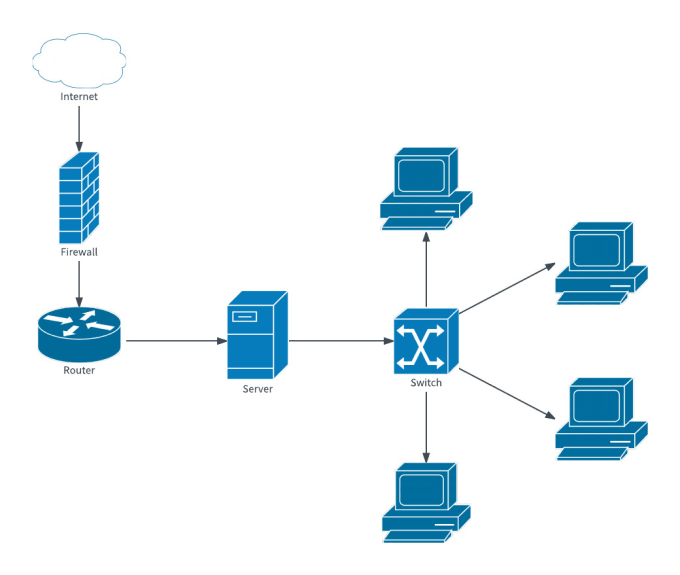
Image: Types of devices involved in Network Security Auditing
4 things to check while performing Network Security Audit
Even though a network security audit isn’t a small task, still right here are a few suggestions that one should check at the same time as acting a network safety audit.
1.Password Security
2.Internal Network Security
- Proper access permissions
- Disable guest accounts
- Logs for unauthorized login attempts
3.Firewall Security
- NAT implementation
- Inbound network rules
- Firewall policies for security risks.
4.Mobile Devices Security
- Connected devices should be encrypted
- List of applications installed for verification of insecure apps.
How is Network Security Audit performed?
Network security audits are done in 5 simple steps. Let’s understand all of them in detail:
Step 1: Identify all the devices
Endpoint safety is a first-rate challenge for maximum organizations as it is hard to become aware of and track all of the devices on the community. With an powerful community security audit, you can identify the endpoint gadgets and their vulnerabilities.
The audit should offer a community diagram that identifies the gadgets and working structures. This facts can help an auditor find endpoints and their vulnerabilities.
Step 2: Identify Network Policies
While a Network audit is being planned, a organization desires to make certain that they truly understand all the security regulations and approaches in location. Protection policies and processes are a extensive part of a network audit.
These guidelines and methods are what an auditor will use to decide if a employer complies with the hints set forth by means of the enterprise this is being audited. further, security guidelines and techniques can also be used to discover if any areas need to be updated.
Step 3: Risk Assessment
A hazard evaluation is a system that identifies the dangers that an entity faces in its operations and the ability outcomes of the risks at the entity, its control, and its stakeholders.
Threat tests can be conducted on an ongoing basis to perceive new risks, monitor modifications in risks, and assist to decide the perfect manipulate surroundings. Hazard assessment is one of the center elements of an incorporated control software.
Step 4: Network Penetration Testing
Network penetration testing out is the practice of checking out a network to discover vulnerabilities that an outside intruder may exploit.
While you behavior a community penetration take a look at, you commonly have greater time and resources at your disposal to check all components and facets of the network. Community penetration trying out is a commonplace method for ensuring that a community is at ease. All groups and authorities organizations require network penetration checking out earlier than they may approve a device’s security.
Step 5: Reporting
Reporting is the final section within the community protection audit. It enables management to evaluate the risks of the internal and external protection threats to their corporations. usually, the auditing crew prepares a record in their findings. The report includes a detailed precis of the findings and a complete list of the risks of the internal and outside safety threats.
Tools used to perform Network Security Audit
` Some of the most popular tools used to perform network security audit are:
Some of the most popular tools used to perform network security audit are:
Nmap
Wireshark
Metasploit
Kismet
These are some of the most used tools that are used to perform network security audits.
Why CyberCure for Networks Audits?
With rich experience of more than one hundred network security clients, CyberCure is one of the great community Audit corporations in India, its top goal is to help the industry to permit them to behavior their commercial enterprise in a greater at ease, efficient and effortless way, hold the Confidentiality, Integrity and Availability of the treasured facts and decrease enterprise losses precipitated due to numerous community threats & assaults.
CyberCure possesses widespread revel in in accomplishing VAPTs throughout numerous groups in India. CyberCure network Audits will discover the digital vulnerabilities that your business is going through and offer pointers to make certain right security controls are integrated into your era environment.
CyberCure in-intensity community Audit facilitates you achieve powerful danger control and safety compliance from cyber threats.
Feel free to get in touch.
Looking for something Else?
Consulting
- Extensive Web Application Security Testing (WEB VAPT)
- ISO 27001:2013 Audit and Certification
- GDPR, CCPA Rediness Audits
- IT Process Audit
- Network Security Audit
- Mobile Application Security Audit (VAPT)
- Firewall Assessment - Policies Audit
- Cyber Crime Investigation
- Employee IT Security Awareness programs
Services
Solutions