single-sign-on-solutions
Single sign-on (SSO) is one of several authentication technology aimed toward streamlining and retaining login information and approaches secure. SSO makes it feasible for one login to be enough for a group of associated websites and applications.
it’s far regularly implemented at the side of multi-aspect authentication (MFA), in which more than one aspect of authentication is needed to authenticate the user. further to a password, the user wishes a pin, a bodily token or key, a code despatched to a telephone, or a few type of biometric input. consequently, if the SSO login is compromised, MFA operates as an additional layer of security.
What is Single Sign-On?
It eliminates the need for users to go into usernames and passwords for person applications and systems. rather, they sincerely check in once and the answer communicates the ideal credentials to the separate packages and structures.
single sign-on can be a part of a password control device if the device acts as a vital consider broker for a device or agency, as opposed to really “vaulting,” or storing, multiple passwords.
some SSO solutions run on-premises, even as others run in the cloud, and some provide more than one deployment options. however the cloud is increasingly more becoming the desired choice for SSO. most providers offer at the least a software-as-a-provider (SaaS) choice on pinnacle of on-premises software program services. And a range of at the moment are favoring SaaS-only SSO.
In line with Gartner, SaaS is with the aid of some distance the biggest increase place of SSO and has become the dominant model. as a consequence, companies hoping to carry out properly will need to offer cloud-primarily based SSO offerings.
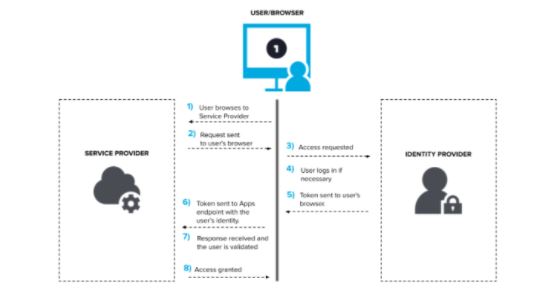
How does Single Sign-On work?
SSO may be completed in various methods, however the most commonplace method is federation; the user logs into an identification issuer (IDP) provider. The IDP hands off a token, declaration, or price ticket to an software with a purpose to gain get entry to with out asking the user to re-authenticate. Kerberos, security announcement Markup Language (SAML), OAuth and OpenID connect (OIDC) are a number of the commonplace federation technologies.
SSO can both be sold as a standalone product or as part of an identification and get entry to management (IAM) or security suite. unmarried signal-on is regularly bundled with get right of entry to manipulate, centralized authentication, consultation control, authorization enforcement, multi-element authentication, and different features.
more and more. authentication structures follow concepts of 0 agree with – permitting customers get entry to handiest to those sources and privilege degrees they need. And passwordless authentication techniques are also developing in importance, given the security limitations of passwords.
Gartner sees access management subsequently turning into approximately decentralized identification. instead of a user-focused device of identity and verification, an “identity believe cloth” will provide a layer of safety between users and programs – a idea not that a long way removed from SSO. That evolution will take time, but.
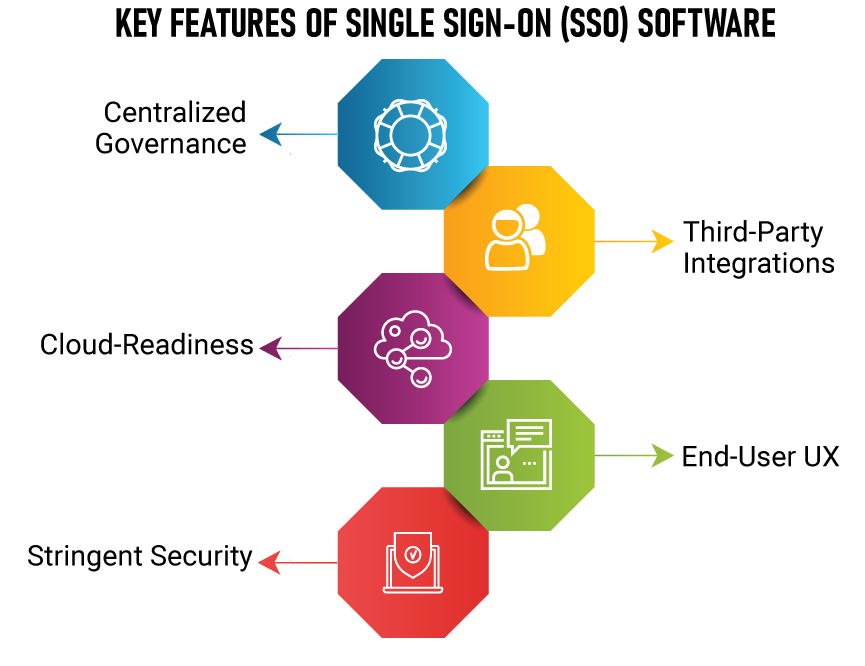
Key Single Sign-On Features
At its middle, SSO is in reality approximately supplying users exact virtual get right of entry to experiences across packages. Ease of use, then, is a key element along side pace of deployment.
At a naked minimal, SSO should provide a standards-based manner to guide numerous provisioning use instances and effortlessly connect to programs. similarly capabilities encompass out-of-the-field flows, passwordless aid, and assist for an expansion of user stores and programs (each on-premises and SaaS).
increasingly more, users are disturbing that SSO equipment are SaaS-delivered and drag-and-drop intuitive. SSO solutions must additionally provide authentication abilities inclusive of FIDO, OTP, and push authentications. And an SSO solution should be capable of provide seamless stories that allow users to effortlessly register new customers, song their consent, and give them self-carrier talents inclusive of incorporated password reset or profile and consent control.
“It’s not enough to definitely permit all requirements-based programs to be a viable SSO answer,” said Matthew Berzinski, senior director of product control at ForgeRock. “supporting OAuth, OIDC, and SAML are table stakes.
“As legacy clients go through digital variations, they need so one can allow SSO for legacy applications with token trade and shape fill.”
Top Single Sign-On Providers & Solutions
ForgeRock Identity Platform
The AI-powered ForgeRock Identity Platform includes full-suite identity and access management (IAM) and identity governance and administration (IGA) capabilities. It can be implemented across an organization for all identities (workforce, consumers, and more), and it offers feature parity across all delivery options, including on-premises, any cloud environment, multi-cloud, hybrid, and as-a-service.
Key Differentiators
- Contextual and adaptive authentication, including usernameless and passwordless
- Data isolation technology gives full control of services
- Granular data residency with regional availability to make compliance easier
- Dedicated services within a multi-tenant cloud service to ensure maximum performance
- Enterprise-wide risk visibility with AI-driven access reviews and approvals
- Intelligent access trees allow the infusion of context and choice into every step of the user journey
Ping
 PingOne Cloud’s SSO capabilities are a core part of the platform. Since SSO is critical to both internal and external identity use cases, Ping Identity includes SSO capabilities with PingOne for customers or PingOne for Workforce solution packages. Ping Identity’s SSO solutions support a variety of standards and out-of-the-box integrations, and they connect to many types of applications no matter where they are hosted.
PingOne Cloud’s SSO capabilities are a core part of the platform. Since SSO is critical to both internal and external identity use cases, Ping Identity includes SSO capabilities with PingOne for customers or PingOne for Workforce solution packages. Ping Identity’s SSO solutions support a variety of standards and out-of-the-box integrations, and they connect to many types of applications no matter where they are hosted.
Key Differentiators
- Seamless access to SaaS, mobile, cloud, and enterprise apps with one set of credentials
- Cloud or on-premises deployment options
- Adds risk and fraud signals as well as SSO capabilities
- Serves more than half of the Fortune 100
- Can incorporate non-standards-based apps, apps spread across multiple clouds, and on-premises environments
Azure
 Microsoft Azure AD provides a frictionless user experience for single sign-on and a simplified app deployment with a centralized user portal. It can enforce strong risk-based access policies with identity protection and conditional access.
Microsoft Azure AD provides a frictionless user experience for single sign-on and a simplified app deployment with a centralized user portal. It can enforce strong risk-based access policies with identity protection and conditional access.
Key Differentiators
- Automated provisioning workflows and self-service tools to help reduce IT costs
- Unburden users of having to memorize credentials for different apps or reusing weak passwords, increasing the risk of data breach
- Access all apps from any location, on any device, from a centralized and branded portal
- Automated user provisioning and de-provisioning
- Measure the user, location, and device risk to determine whether access should be allowed, verified, limited, or blocked
- Self-service password reset
IBM
 IBM Security Access Manager is an authentication and authorization solution for corporate web, client/server, and existing applications. It controls user access to protected information and resources. By providing a centralized, flexible, and scalable access control solution, Security Access Manager builds secure and easy-to-manage network-based applications and infrastructure.
IBM Security Access Manager is an authentication and authorization solution for corporate web, client/server, and existing applications. It controls user access to protected information and resources. By providing a centralized, flexible, and scalable access control solution, Security Access Manager builds secure and easy-to-manage network-based applications and infrastructure.
Key Differentiators
- Supports authentication, authorization, data security, and resource management
- Uses a wide range of built-in authenticators and supports external authenticators
- The authorization service, accessed through an API, provides permit and deny decisions on access requests for native Security Access Manager servers and other applications
- Existing applications can take advantage of the Security Access Manager authorization service and provide a common security policy for the entire enterprise
- Controls user and group participation in the domain and applies rules to resources that determine the security policy for a domain. These rules are defined by access control lists (ACLs), protected object policies (POPs), and authorization rules
Looking for something Else?
Consulting
- Extensive Web Application Security Testing (WEB VAPT)
- ISO 27001:2013 Audit and Certification
- GDPR, CCPA Rediness Audits
- IT Process Audit
- Network Security Audit
- Mobile Application Security Audit (VAPT)
- Firewall Assessment - Policies Audit
- Cyber Crime Investigation
- Employee IT Security Awareness programs
Services
Solutions