Web Application Security Testing (WEB VAPT)
What Is Web VAPT or Web Application Security Testing?
 Vulnerability Assessment and Penetration testing (VAPT) are strategies used for internet site security. The tests frequently mixed to achieve a more whole vulnerability analysis. Vulnerability checks and Penetration testing carry out unique tasks, typically with different outcomes, inside the equal vicinity of attention.
Vulnerability Assessment and Penetration testing (VAPT) are strategies used for internet site security. The tests frequently mixed to achieve a more whole vulnerability analysis. Vulnerability checks and Penetration testing carry out unique tasks, typically with different outcomes, inside the equal vicinity of attention.
Vulnerability assessment discovers vulnerabilities, however cannot differentiate between flaws that could purpose damage after being exploited. Vulnerability scanner document businesses approximately flaws in their code and in which they’re located. In Penetration testing strive are made to take advantage of the vulnerabilities to determine whether or not unauthorized get right of entry to or other malicious activities inside the web application. Penetration checks locate exploitable flaws severity of exploitable of every. together, Penetration testing and Vulnerability assessment provide an in depth picture of the failings that exist in internet software and the dangers associated with the ones flaws.
What Are The Signs That A Website Has Been Hacked?
Internet site hacking is turning into a serious problem each day. Attackers are getting very superior and tactical with their modus operandi and subsequently it becomes crucial to shield your web sites and discover any malicious activity in time.
Every interest leaves a path and it’s far essential to look for the proper signs and symptoms. in case you see following signs and symptoms it is time you are taking a tough examine your website.
• Your internet site turns into very gradual and starts popping error messages.
• Browser warns consumer of malicious hobby earlier than redirecting to your internet site.
• net site disappears from Google.
• Google search console informs you of malware or malicious hobby on your website.
• Your website would possibly redirect consumer to any other internet site.
What Can A Malicious Website Do?
A malicious internet site is any website that’s been designed to cause damage. In this newsletter, we’ll awareness on phishing web sites and malware web sites.
 A phishing website – now and again called a “spoof” or “lookalike” internet site – steals your records. Phishing websites seem like legitimate websites. however, while site visitors are brought about to go into login credentials, non-public records, or credit card information, the statistics is directed to cybercriminals.
A phishing website – now and again called a “spoof” or “lookalike” internet site – steals your records. Phishing websites seem like legitimate websites. however, while site visitors are brought about to go into login credentials, non-public records, or credit card information, the statistics is directed to cybercriminals.
Looking for an example? A researchers observed seventy five domains spoofing web sites associated with mail-in vote casting in August. For more records, study this text: the way to avoid Falling sufferer to balloting Scams within the 2020 Election. In this example, attackers have been after in my opinion identifiable data (PII) and credit score card details.
once a phishing internet site collects your records, it could be utilized in hacking operations and further phishing attacks, or bought at the darkish internet.
A malware internet site, then again, installs malicious software to your tool. even as this could take place after the visitor downloads an software or document, it can additionally show up without the vacationer even noticing.
Why deploy malware? Malicious software program can serve many specific purposes, along with extracting information from someone’s tool, taking manipulate of the tool, or the use of the device as an entry point into a network. But phishing and malware sites aren’t the most effective troubles. Different websites, which include fake news and disinformation websites, can also be considered malicious web sites. these web sites intention to unfold discord, affect election results, and disrupt the activities of human rights companies.
What Is The Purpose Of Web Security?
The net is a risky vicinity! With terrific regularity, we pay attention about websites becoming unavailable because of denial-of-service assaults, or showing changed (and frequently damaging) data on their homepages. In other excessive-profile instances, tens of millions of passwords, email addresses, and credit card information have been leaked into the general public area, exposing website users to both non-public embarrassment and economic chance.
The purpose of internet site protection is to prevent these (or any) types of assaults. The more formal definition of internet site security is the act/practice of protective websites from unauthorized get admission to, use, modification, destruction, or disruption.
WHY WEB APPLICATION PENTESTING (VAPT) IS ESSENTIAL?
Internet servers and the software code going for walks on those as a easy website or net portal, are vulnerable to various assaults. in a single type of assault, the hacker can in reality deface the pages, whilst in different extreme types, the attacker can potentially scouse borrow records and disrupt internet site operations.
web protection checking out is in particular essential in case of e-commerce primarily based portals, wherein the entire enterprise is predicated on website and its facts contents. In case of new trend the websites cater to mobile based totally packages which needs for an quit to cease checking out for general app safety. Its crucial to keep in mind that merely having firewalls and Layer-7 gadgets aren’t sufficient because those can not hit upon code stage vulnerabilities, and for this reason a detailed website VAPT in conjunction with code protection evaluation is notably endorsed.
What Are The Common Tools Applications Used In Web Security?
Detail about some of the most popular tools in the field of Cyber Security.
Kali Linux
 Kali Linux is a few of the most commonplace tools utilized in Cyber security. This working gadget consists of a number gear which might be beneficial in protection auditing, network and machine scanning for vulnerabilities, etc. one of the important blessings of this platform is that Cyber protection experts with distinct tiers of information can use it, making it an ideal desire even for entry-degree experts. Except, a variety of the equipment offered by using Kali Linux are without problems executable, allowing users to monitor the business enterprise’s network protection structures the usage of a single click on.
Kali Linux is a few of the most commonplace tools utilized in Cyber security. This working gadget consists of a number gear which might be beneficial in protection auditing, network and machine scanning for vulnerabilities, etc. one of the important blessings of this platform is that Cyber protection experts with distinct tiers of information can use it, making it an ideal desire even for entry-degree experts. Except, a variety of the equipment offered by using Kali Linux are without problems executable, allowing users to monitor the business enterprise’s network protection structures the usage of a single click on.
Metasploit
 Metasploit has an excellent collection of tools that are perfect for penetration testing. Professionals often use it to meet a range of security objectives, such as discovering vulnerabilities of systems and networks, designing strategies to improve the company’s Cyber Security defenses, and more. Metasploit enables experts to test system security of online and web-based applications, servers, networks, etc. One of the advantages of this software is that it can uncover even emerging weaknesses and provide top-notch security round the clock.
Metasploit has an excellent collection of tools that are perfect for penetration testing. Professionals often use it to meet a range of security objectives, such as discovering vulnerabilities of systems and networks, designing strategies to improve the company’s Cyber Security defenses, and more. Metasploit enables experts to test system security of online and web-based applications, servers, networks, etc. One of the advantages of this software is that it can uncover even emerging weaknesses and provide top-notch security round the clock.
Burpsuite
 Burp Suite is a robust device used in the area of Cyber security that allows groups to decorate their network safety. protection specialists use Burp Suite to perform actual-time scans on structures focusing on identifying essential vulnerabilities which can have a big impact on the organization’s security. furthermore, it simulates attacks to find the distinctive methods wherein these threats can weaken and compromise the security of the community. Burp Suite has three versions, namely, network, professional, and organization. The network model of Burp Suite is available without cost, but loads of capabilities are restrained and can not be used in this model. It best gives the critical guide tools. The expert and employer versions of Burp Suite are for industrial use, and hence, they’re no longer available totally free use. although it is able to be a bit expensive for small groups, Burp Suite is the various top picks of security tools for maximum businesses.
Burp Suite is a robust device used in the area of Cyber security that allows groups to decorate their network safety. protection specialists use Burp Suite to perform actual-time scans on structures focusing on identifying essential vulnerabilities which can have a big impact on the organization’s security. furthermore, it simulates attacks to find the distinctive methods wherein these threats can weaken and compromise the security of the community. Burp Suite has three versions, namely, network, professional, and organization. The network model of Burp Suite is available without cost, but loads of capabilities are restrained and can not be used in this model. It best gives the critical guide tools. The expert and employer versions of Burp Suite are for industrial use, and hence, they’re no longer available totally free use. although it is able to be a bit expensive for small groups, Burp Suite is the various top picks of security tools for maximum businesses.
Sqlmap
 Sqlmap is an open supply penetration checking out device that automates the process of detecting and exploiting sql injection flaws and taking over of database servers. It comes with a effective detection engine, many area of interest features for the last penetration tester and a huge variety of switches lasting from database fingerprinting, over facts fetching from the database, to accessing the underlying report device and executing instructions at the running device through out-of-band connections.
Sqlmap is an open supply penetration checking out device that automates the process of detecting and exploiting sql injection flaws and taking over of database servers. It comes with a effective detection engine, many area of interest features for the last penetration tester and a huge variety of switches lasting from database fingerprinting, over facts fetching from the database, to accessing the underlying report device and executing instructions at the running device through out-of-band connections.
Nikto
 Scan your net web site and server without delay with the popular Nikto net Scanner. This testing provider can be used to check a web web page, virtual Host and web Server for known security vulnerabilities and mis-configurations. Nikto plays over 6000 assessments against a website. The massive range of assessments for both security vulnerabilities and mis-configured internet servers makes it a visit device for lots security professionals and structures directors. it may discover forgotten scripts and other difficult to come across troubles from an external perspective.
Scan your net web site and server without delay with the popular Nikto net Scanner. This testing provider can be used to check a web web page, virtual Host and web Server for known security vulnerabilities and mis-configurations. Nikto plays over 6000 assessments against a website. The massive range of assessments for both security vulnerabilities and mis-configured internet servers makes it a visit device for lots security professionals and structures directors. it may discover forgotten scripts and other difficult to come across troubles from an external perspective.
What Are Web Application Attacks?
An internet software attack is any strive through a malicious actor to compromise the security of an internet-primarily based software. Web software assaults might also target either the utility itself to benefit get entry to to sensitive information, or they may use the application as a staging publish to release attacks against users of the software.
What are common Web application attack?
Cross site scripting (xss)]
cross-site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into in any other case benign and depended on web sites. XSS assaults occur whilst an attacker makes use of a web software to send malicious code, commonly in the shape of a browser aspect script, to a exceptional stop user. Flaws that permit these attacks to prevail are quite great and occur everywhere an internet utility uses enter from a person inside the output it generates without validating or encoding it.
SQL INJECTION
Sql injection, additionally known as SQLI, is a not unusual assault vector that uses malicious sql code for backend database manipulation to get entry to facts that turned into now not supposed to be displayed. This records might also encompass any wide variety of objects, which include touchy organization facts, user lists or personal patron info.
The effect square injection can have on a business is far-reaching. A successful assault can also bring about the unauthorized viewing of person lists, the deletion of complete tables and, in positive instances, the attacker gaining administrative rights to a database, all of which are extraordinarily damaging to a business.
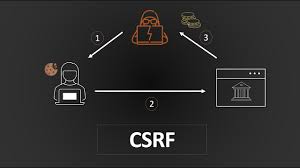
CROSS SITE REQUEST FORGERY (CSRF)
Cross-site Request Forgery (CSRF) is an assault that forces an stop consumer to execute undesirable actions on an internet software in which they’re presently authenticated. With a little assist of social engineering (inclusive of sending a hyperlink through e mail or chat), an attacker may trick the users of an internet software into executing movements of the attacker’s deciding on. If the victim is a regular person, a successful CSRF attack can force the user to perform kingdom converting requests like shifting funds, changing their email address, and so on. If the sufferer is an administrative account, CSRF can compromise the whole net software.
DENIAL -OF SERVICE (DOS)
The Denial of service (DoS) attack is focused on making a aid (site, application, server) unavailable for the cause it turned into designed. there are numerous approaches to make a provider unavailable for valid customers by using manipulating network packets, programming, logical, or resources handling vulnerabilities, amongst others. If a provider gets a very large variety of requests, it may give up to be to be had to valid users. in the identical manner, a service can also prevent if a programming vulnerability is exploited, or the way the carrier handles sources it uses.
DISTRIBUTED DENIAL OF SERVICE (DDOS)
A distributed denial of service (DDoS) assault is while an attacker, or attackers, attempt to make it not possible for a service to be delivered. this can be executed through thwarting access to absolutely whatever: servers, devices, offerings, networks, packages, or even specific transactions within packages
OWASP Top 10 Attacks
OWASP top 10 is a standard awareness report for developers and net utility security. It represents a wide consensus approximately the maximum crucial safety risks to web applications.
organizations need to adopt this record and begin the procedure of making sure that their web programs reduce those risks. the use of the OWASP top 10 is possibly the only first step closer to converting the software improvement lifestyle inside your agency into one that produces greater at ease code.
1. Injection
Injection happens whilst an attacker exploits insecure code to insert (or inject) their very own code into a application. Because this system is unable to determine code inserted in this way from its very own code, attackers are capable of use injection attacks to get entry to cozy areas and private information as even though they may be relied on customers. Examples of injection include square injections, command injections, CRLF injections, and LDAP injections. Utility safety checking out can display injection flaws and suggest remediation techniques together with stripping unique characters from consumer enter or writing parameterized sql queries.
2. Broken Authentication
Incorrectly carried out authentication and consultation management calls can be a large protection risk. If attackers be aware those vulnerabilities, they’ll be capable of without problems assume legitimate customers’ identities. Multifactor authentication is one way to mitigate damaged authentication. put in force DAST and SCA scans to come across and get rid of issues with implementation errors before code is deployed.
3. Sensitive data exposure
APIs, which allow builders to attach their utility to 1/3-celebration services like Google Maps, are extremely good time-savers. but, a few APIs depend upon insecure information transmission techniques, which attackers can exploit to gain get admission to to usernames, passwords, and different touchy information. statistics encryption, tokenization, proper key management, and disabling reaction caching can all assist reduce the risk of touchy records exposure.
4. XML external Entities
This hazard takes place whilst attackers are able to add or consist of antagonistic XML content material because of insecure code, integrations, or dependencies. An SCA test can discover risks in third party additives with recognised vulnerabilities and could warn you approximately them. Disabling XML external entity processing additionally reduces the likelihood of an XML entity assault.
5. Broken access control
If authentication and get admission to restriction are not properly applied, it is easy for attackers to take whatever they need. With broken get admission to control flaws, unauthenticated or unauthorized customers may have access to touchy files and structures, or even person privilege settings.
Configuration mistakes and insecure get right of entry to manage practices are hard to locate as computerized tactics can not constantly test for them. Penetration trying out can hit upon lacking authentication, but different methods ought to be used to decide configuration troubles. weak get right of entry to controls and troubles with credentials control are preventable with secure coding practices, as well as preventative measures like locking down administrative bills and controls and the use of multi-component authentication.
6. Security Misconfiguration
Much like misconfigured get right of entry to controls, greater general protection configuration mistakes are huge dangers that supply attackers short, smooth get entry to to touchy data and location areas. Dynamic trying out will let you discover misconfigured safety for your software.
7. Cross-site Scripting
With pass-web page scripting, attackers take advantage of APIs and DOM manipulation to retrieve statistics from or ship instructions on your application. pass-web site scripting widens the attack surface for chance actors, permitting them to hijack consumer money owed, get right of entry to browser histories, spread Trojans and worms, manage browsers remotely, and greater. schooling developers in excellent practices such as facts encoding and input validation reduces the likelihood of this hazard. Sanitize your statistics by using validating that it’s the content you count on for that specific subject, and by means of encoding it for the “endpoint” as a further layer of protection.
8. Insecure Deserialization
Deserialization, or retrieving information and items which have been written to disks or in any other case stored, may be used to remotely execute code to your software or as a door to similarly assaults. The format that an object is serialized into is either dependent or binary textual content via not unusual serialization systems like JSON and XML. This flaw happens while an attacker uses untrusted data to govern an application, provoke a denial of carrier (DoS) attack, or execute unpredictable code to alternate the conduct of the utility. Despite the fact that deserialization is tough to take advantage of, penetration testing or the use of application protection equipment can reduce the risk further. moreover, do no longer be given serialized gadgets from untrusted sources and do now not use strategies that simplest permit primitive statistics types.
9. Use of components with known Vulnerabilities
Irrespective of how at ease your own code is, attackers can exploit APIs, dependencies and other 1/3-party components if they are not themselves secure. Astatic analysis accompanied via a software composition analysis can discover and help utralize insecure components to your application. Veracode’s static code analysis tools can assist builders find such insecure components of their code before they publish an software.
10. Insufficient Logging and monitoring
Failing to log errors or assaults and negative monitoring practices can introduce a human element to protection risks. Threat actors assume a loss of monitoring and slower remediation instances with a view to carry out their assaults before you’ve got time to notice or react. To save you issues with insufficient logging and tracking, make certain that every one login disasters, get admission to manipulate screw ups, and server-aspect enter validation disasters are logged with context so you can pick out suspicious activity. Penetration checking out is a exquisite way to discover areas of your application with inadequate logging too. Establishing effective monitoring practices is also essential.
What Is Web Server Security?
Web server security refersthe equipment, technology and methods that allow information security (IS) on a web server. This broad term encompasses all techniques that make sure that a running internet server operates beneath a safety policy.
Web server security is the safety of any server this is deployed on a worldwide internet domain or the internet. it’s far applied through several techniques and in layers, normally, consisting of the bottom operating gadget (OS) protection layer, hosted application safety layer and community protection layer. OS safety, which ensures access to legal users only, operates a web server’s critical additives and offerings. utility layer security ensures manipulate over the content and services hosted on the web server. Network security affords protection towards net-based totally protection exploits, viruses and assaults.
secure Sockets Layer (SSL) certificate, HTTP comfy protocol and firewalling are numerous gear and technology used to put in force internet server security.
What Are The Most Important Steps Recommended For Securing A New Web Server?
To installation a secure new web server, or improve the safety of your commercial enterprise’s existing internet servers, there are several simple steps you could take.
Remove needless services
Default working structures and configurations lack complete safety. Generally talking, there are numerous community offerings protected in a default installation that gained’t be used, from remote registry services to print server service and different capabilities. The greater offerings you have got running for your server running machine, the greater ports are left open – meaning extra doorways into the community that a malicious hacker ought to exploit. as well as assisting with security, disposing of needless offerings also can increase your server overall performance.
Create separate environments for development, testing, and production
Growing and checking out are often accomplished on production servers, that is why you may sometimes stumble upon websites or pages on-line that function info like /new/ or /test/ in the URL. web packages which might be in their early improvement levels will frequently have security vulnerabilities and may be exploited the usage of freely to be had on line tools. you may help to limit the threat of a breach with the aid of keeping development and trying out to servers remoted from the general public internet, and no longer connecting them to crucial information and databases.
Set permissions and privileges
Network provider permissions, and file permissions, play a critical position for your community protection. in case your web server is compromised via network carrier software program, the awful actor can use whichever account the network service is strolling to carry out obligations. because of this, the simple act of setting minimal privileges for customers to get right of entry to internet app files and back end databases can be instrumental in preventing loss or manipulation of data.
Maintain patches updated
As noted earlier in this text, failure to hold software program updated with the modern day patches can allow cybercriminals to reverse-engineer pathways into your network.
Segregate and display server logs
As a part of your regular security testing, store your server logs in segregation, and reveal and test them frequently. unusual log file entries reveal statistics about attempted and successful assaults and should be investigated as and when they stand up.
set up a firewall
software program-primarily based firewalls are easy to installation and manage and will guard your net servers from unauthorized verbal exchange and intrusions.
Automate backups
Making everyday server backups guarantees that if your safety defenses are compromised, you may recover and repair data speedy. Automation can enhance performance, however an IT employee need to take a look at for issues that can have interrupted the method.
Why CyberCure for web VAPT?
With rich experience of greater than 100 web protection customers, CyberCure is one of the best web VAPT organizations in India, its top objective is to assist the enterprise to enable them to behavior their business in a greater relaxed, green and easy manner, hold the Confidentiality, Integrity and Availability of the valuable statistics and decrease enterprise losses prompted due to numerous information threats & assaults.
CyberCure possesses vast experience in engaging in VAPTs throughout numerous agencies in India. CyberCure VAPT auditors make use of confirmed and widespread evaluation methodologies, consulting and project control methodologies to deliver accurate and timely outcomes to your organization’s IT branch. With our net app VAPT capabilities, it allows you to control a prioritized listing of recognized vulnerabilities in your website and apprehend the way to restoration them so you are ensured to be one step ahead of a likely attacker.
CyberCure VAPT services are intended for the first-rate process, easy & devoted to delivering inside the agreed timelines.
Feel free to get in touch.
Looking for something Else?
Consulting
- Extensive Web Application Security Testing (WEB VAPT)
- ISO 27001:2013 Audit and Certification
- GDPR, CCPA Rediness Audits
- IT Process Audit
- Network Security Audit
- Mobile Application Security Audit (VAPT)
- Firewall Assessment - Policies Audit
- Cyber Crime Investigation
- Employee IT Security Awareness programs
Services
Solutions